Background
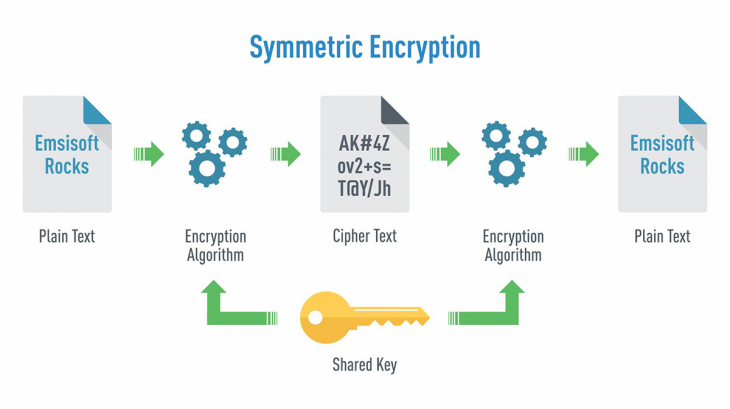
Many IoT devices communicate with other devices over a wireless network. Since in principle anyone within radio range can receive the communication, it is important that this communication is encrypted. In frequently used IoT protocols like LoRaWAN, ZigBee or Z-Wave encryption methods are already built in. Without knowledge of the corresponding key, it is no longer possible to know the contents of the communication or to send one's own packets into the network. Some protocols like ZigBee [1] even use the same key for each participant.
This makes it all the more important that the devices connected to the network do not reveal the key. Ideally, the keys should be stored in a secure element [2], in the worst case the key material is stored on a flash memory in the device, which is easy to read with the corresponding hardware [3].
Task description
The following questions should be answered:
- How are user data secured in widespread IoT protocols?
- What effects would key theft have on the communication of the respective protocols?
- What precautions can be taken to secure the key in the devices?
For further investigation, we can purchase IoT devices as examples, which can then be used to carry out practical attacks on the key material.
Literature
1: ZigBee Specification, ZigBee Standard Organisation, http://www.zigbee.org/wp-content/uploads/2014/11/docs-05-3474-20-0csg-zigbee-specification.pdf
2: What is a Secure Element?, Gemalto NV, https://www.justaskgemalto.com/en/what-is-a-secure-element/
3: Reverse Engineering Flash Memory for Fun and Benefit, Jeong Wook (Matt) Oh, https://www.blackhat.com/docs/us-14/materials/us-14-Oh-Reverse-Engineering-Flash-Memory-For-Fun-And-Benefit-WP.pdf
4: Galen Hunt, George Letey und Ed Nightingale. “The seven properties of highly secure devices”. In: tech. report MSR-TR-2017-16 (2017).
5: H. Ju u. a. “Implementation of a hardware security chip for mobile devices”. In: IEEE Transactions on Consumer Electronics 61.4 (Nov. 2015), S. 500–506. issn: 0098-3063. doi: 10.1109/TCE.2015.7389805.
6: NIST FIPS Pub. 140-2: Security requirements for cryptographic modules. Techn. Ber. Federal information processing standards publication, Mai 2001. doi: 10.6028/ nist.fips.140-2.